Spring Security之默認的過濾器鏈及自定義Filter操作
過濾器順序從上到下
自定義 Filter自定義的 Filter 建議繼承 GenericFilterBean,本文示例:
package com.example.filter;import org.springframework.web.filter.GenericFilterBean;import javax.servlet.FilterChain;import javax.servlet.ServletException;import javax.servlet.ServletRequest;import javax.servlet.ServletResponse;import java.io.IOException;/** * @author 咸魚 * @date 2019-05-26 18:02 */public class BeforeLoginFilter extends GenericFilterBean { @Override public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws IOException, ServletException {System.out.println('在 UsernamePasswordAuthenticationFilter 前調用');chain.doFilter(request, response); }}配置自定義 Filter 在 Spring Security 過濾器鏈中的位置
配置很簡單,本文示例:
@Override protected void configure(HttpSecurity http) throws Exception {http.authorizeRequests().antMatchers('/').permitAll().antMatchers('/user/**').hasAuthority('USER').and().formLogin().loginPage('/login').defaultSuccessUrl('/user').and().logout().logoutUrl('/logout').logoutSuccessUrl('/login');// 在 UsernamePasswordAuthenticationFilter 前添加 BeforeLoginFilterhttp.addFilterBefore(new BeforeLoginFilter(), UsernamePasswordAuthenticationFilter.class);// 在 CsrfFilter 后添加 AfterCsrfFilterhttp.addFilterAfter(new AfterCsrfFilter(), CsrfFilter.class); }
說明:
HttpSecurity 有三個常用方法來配置:
addFilterBefore(Filter filter, Class<? extends Filter> beforeFilter)
在 beforeFilter 之前添加 filter
addFilterAfter(Filter filter, Class<? extends Filter> afterFilter)
在 afterFilter 之后添加 filter
addFilterAt(Filter filter, Class<? extends Filter> atFilter)
在 atFilter 相同位置添加 filter, 此 filter 不覆蓋 filter
通過在不同 Filter 的 doFilter() 方法中加斷點調試,可以判斷哪個 filter 先執行,從而判斷 filter 的執行順序 。
spring security添加自定義過濾器1、定義自己的過濾器
2、指定位置,通過HttpSecurity的方法指定
定義過濾器package com.qiudaozhang.springsecurity.filter;import javax.servlet.*;import javax.servlet.http.HttpServletRequest;import javax.servlet.http.HttpServletResponse;import java.io.IOException;public class RequestHeadCheckFilter implements Filter { @Override public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {var httpRequest = (HttpServletRequest) servletRequest;var httpResponse = (HttpServletResponse) servletResponse;String requestId = httpRequest.getHeader('Request-id');if(requestId == null || requestId.isBlank()) { httpResponse.setStatus(HttpServletResponse.SC_BAD_REQUEST); return;}filterChain.doFilter(servletRequest,servletResponse); }}
package com.qiudaozhang.springsecurity.filter;import javax.servlet.*;import javax.servlet.http.HttpServletRequest;import javax.servlet.http.HttpServletResponse;import java.io.IOException;public class RequestParamCheckFilter implements Filter { @Override public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {var httpRequest = (HttpServletRequest) servletRequest;var httpResponse = (HttpServletResponse) servletResponse;String timestamp = httpRequest.getParameter('timestamp');if(timestamp == null || timestamp.isBlank()) { httpResponse.setStatus(HttpServletResponse.SC_FORBIDDEN); return;}filterChain.doFilter(servletRequest,servletResponse); }}指定位置
HttpSecurity中有兩個方法,指定過濾器的位置,一個指定在誰前面,一個指定在誰后面。
public HttpSecurity addFilterAfter(Filter filter, Class<? extends Filter> afterFilter) { this.comparator.registerAfter(filter.getClass(), afterFilter); return this.addFilter(filter); } public HttpSecurity addFilterBefore(Filter filter, Class<? extends Filter> beforeFilter) { this.comparator.registerBefore(filter.getClass(), beforeFilter); return this.addFilter(filter); }
package com.qiudaozhang.springsecurity.config;import com.qiudaozhang.springsecurity.filter.RequestHeadCheckFilter;import com.qiudaozhang.springsecurity.filter.RequestParamCheckFilter;import org.springframework.context.annotation.Configuration;import org.springframework.security.config.annotation.web.builders.HttpSecurity;import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;import org.springframework.security.web.authentication.www.BasicAuthenticationFilter;@Configurationpublic class ProjectConfig extends WebSecurityConfigurerAdapter { @Override protected void configure(HttpSecurity http) throws Exception {http.addFilterBefore(new RequestHeadCheckFilter(),BasicAuthenticationFilter.class).addFilterAfter(new RequestParamCheckFilter(),BasicAuthenticationFilter.class).authorizeRequests().anyRequest().permitAll(); }}測試
準備一個端點測試
package com.qiudaozhang.springsecurity.controller;import org.springframework.web.bind.annotation.GetMapping;import org.springframework.web.bind.annotation.RestController;@RestControllerpublic class HelloController { @GetMapping('hello') public String hello () {return 'hello'; }}
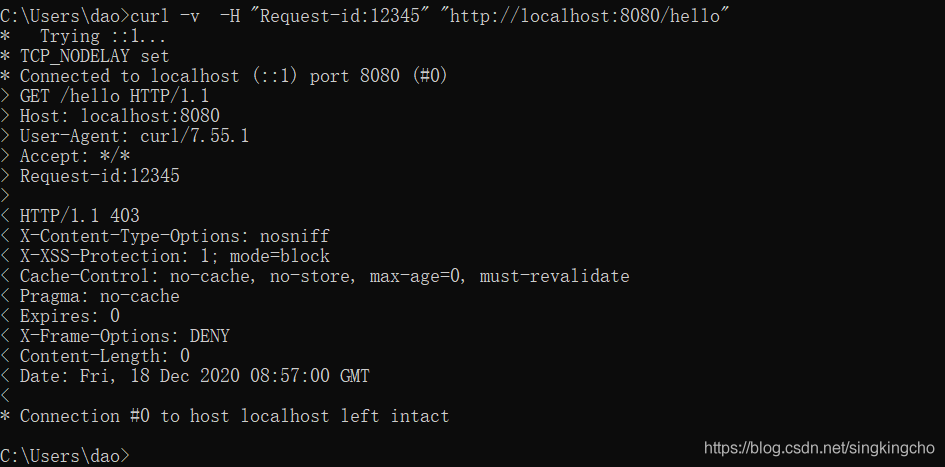
當前沒有傳遞timestamp參數,所以參照約定,過濾器直接給出403.
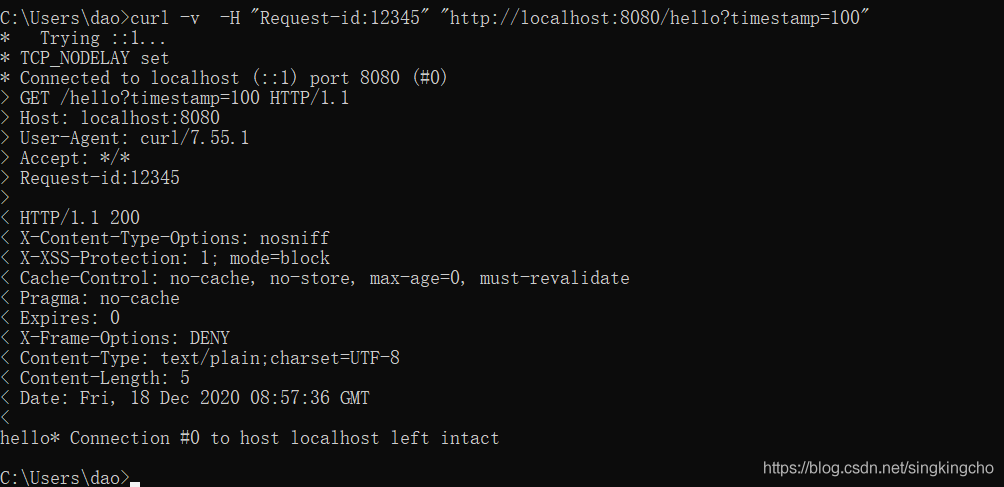
當前頭部信息和參數信息都提供了,檢測通過。
實際應用場景 檢測相關的頭部,參數等等信息日志過濾器,將所有請求的相關數據記錄下來特殊的權限校驗等等。
以上為個人經驗,希望能給大家一個參考,也希望大家多多支持好吧啦網。
相關文章:
1. React+umi+typeScript創建項目的過程2. ASP中常用的22個FSO文件操作函數整理3. ASP編碼必備的8條原則4. ASP調用WebService轉化成JSON數據,附json.min.asp5. 三個不常見的 HTML5 實用新特性簡介6. Warning: require(): open_basedir restriction in effect,目錄配置open_basedir報錯問題分析7. SharePoint Server 2019新特性介紹8. 無線標記語言(WML)基礎之WMLScript 基礎第1/2頁9. ASP.NET Core 5.0中的Host.CreateDefaultBuilder執行過程解析10. php測試程序運行速度和頁面執行速度的代碼
 網公網安備
網公網安備