如何通過(guò)Python3和ssl實(shí)現(xiàn)加密通信功能
一、說(shuō)明
1. python標(biāo)準(zhǔn)庫(kù)ssl可實(shí)現(xiàn)加密通信
2. ssl庫(kù)底層使用openssl,做了面向?qū)ο窕脑旌秃?jiǎn)化,但還是可以明顯看出openssl的痕跡
3. 本文先給出python實(shí)現(xiàn)的socket通信,在此基礎(chǔ)上再給出ssl通信以便讀者更方便地看到socket和ssl在python編程中的區(qū)別
4. 說(shuō)到ssl很多人都會(huì)想到https,但本質(zhì)而言ssl是在傳輸層和應(yīng)用層之間新插入的一個(gè)層,根據(jù)不同層無(wú)關(guān)原則ssl和https并沒(méi)有任何綁定關(guān)系,ssl之上完全可以是其他任何應(yīng)用層協(xié)議(比如pop/imap/telnet等等)
二、程序?qū)崿F(xiàn)
2.1 socket通信實(shí)現(xiàn)
客戶端代碼:
import socketclass client_class: def send_hello(self): # 與服務(wù)端建立連接 client_socket = socket.socket(socket.AF_INET,socket.SOCK_STREAM) client_socket.connect((’127.0.0.1’,9999)) # 向服務(wù)端發(fā)送消息 msg = 'do i connect with server ?'.encode('utf-8') client_socket.send(msg) # 接收服務(wù)端返回的消息 msg = client_socket.recv(1024).decode(’utf-8’) print(f'receive msg from server : {msg}') client_socket.close()if __name__ == '__main__': client = client_class() client.send_hello()
服務(wù)端代碼:
import socketclass server_class : def build_listen(self): # 監(jiān)聽(tīng)端口 server_socket = socket.socket(socket.AF_INET,socket.SOCK_STREAM) server_socket.bind((’127.0.0.1’,9999)) server_socket.listen(5) while True: # 接收客戶端連接 client_socket, addr = server_socket.accept() # 接收客戶端信息 msg = client_socket.recv(1024).decode('utf-8') print(f'receive msg from client {addr}:{msg}') # 向客戶端發(fā)送信息 msg = f'yes , you have client_socketect with server.rn'.encode('utf-8') client_socket.send(msg) client_socket.close()if __name__ == '__main__': server = server_class() server.build_listen()
2.2 ssl通信實(shí)現(xiàn)
客戶端代碼:
import socketimport sslclass client_ssl: def send_hello(self,): # 生成SSL上下文 context = ssl.SSLContext(ssl.PROTOCOL_TLS_CLIENT) # 加載信任根證書 context.load_verify_locations(’cert/ca.crt’) # 與服務(wù)端建立socket連接 with socket.create_connection((’127.0.0.1’, 9443)) as sock: # 將socket打包成SSL socket # 一定要注意的是這里的server_hostname不是指服務(wù)端IP,而是指服務(wù)端證書中設(shè)置的CN,我這里正好設(shè)置成127.0.1而已 with context.wrap_socket(sock, server_hostname=’127.0.0.1’) as ssock: # 向服務(wù)端發(fā)送信息 msg = 'do i connect with server ?'.encode('utf-8') ssock.send(msg) # 接收服務(wù)端返回的信息 msg = ssock.recv(1024).decode('utf-8') print(f'receive msg from server : {msg}') ssock.close()if __name__ == '__main__': client = client_ssl() client.send_hello()
服務(wù)端代碼:
import socketimport sslclass server_ssl: def build_listen(self): # 生成SSL上下文 context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER) # 加載服務(wù)器所用證書和私鑰 context.load_cert_chain(’cert/server.crt’, ’cert/server_rsa_private.pem.unsecure’) # 監(jiān)聽(tīng)端口 with socket.socket(socket.AF_INET, socket.SOCK_STREAM, 0) as sock: sock.bind((’127.0.0.1’, 9443)) sock.listen(5) # 將socket打包成SSL socket with context.wrap_socket(sock, server_side=True) as ssock: while True: # 接收客戶端連接 client_socket, addr = ssock.accept() # 接收客戶端信息 msg = client_socket.recv(1024).decode('utf-8') print(f'receive msg from client {addr}:{msg}') # 向客戶端發(fā)送信息 msg = f'yes , you have client_socketect with server.rn'.encode('utf-8') client_socket.send(msg) client_socket.close()if __name__ == '__main__': server = server_ssl() server.build_listen()
三、運(yùn)行結(jié)果
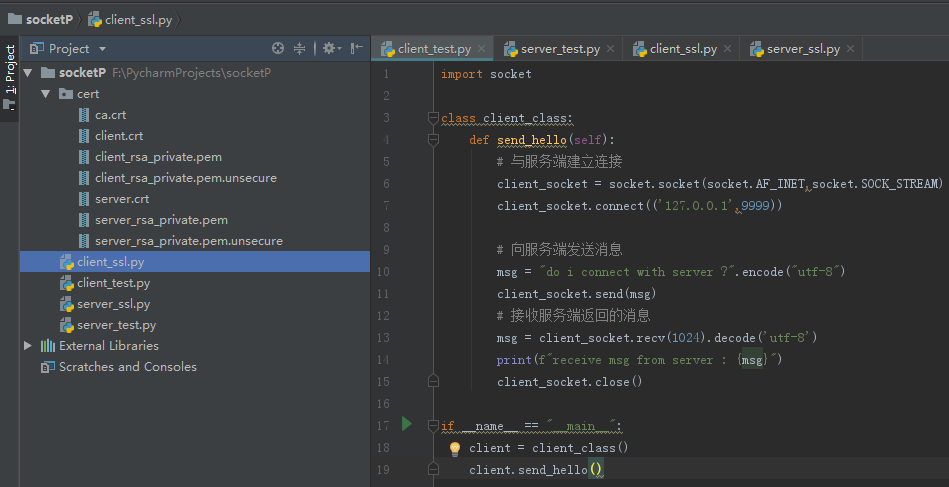
當(dāng)前項(xiàng)目結(jié)構(gòu)如圖所示,證書生成可參考:openssl實(shí)現(xiàn)雙向認(rèn)證教程
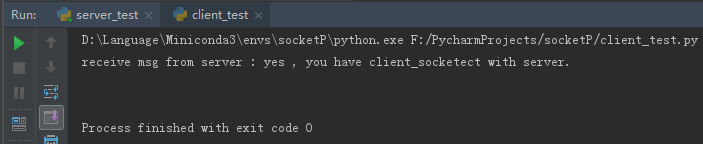
3.1 socket通信運(yùn)行結(jié)果
客戶端:
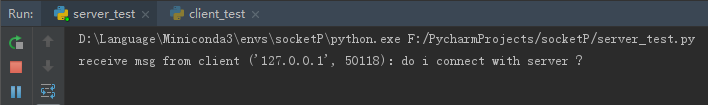
服務(wù)端:
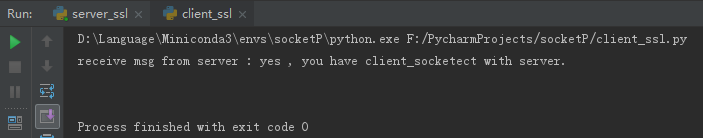
3.2 ssl通信運(yùn)行結(jié)果
客戶端:
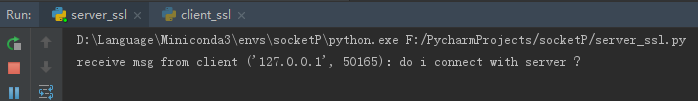
服務(wù)端:
以上就是本文的全部?jī)?nèi)容,希望對(duì)大家的學(xué)習(xí)有所幫助,也希望大家多多支持好吧啦網(wǎng)。
相關(guān)文章:
1. CSS hack用法案例詳解2. css進(jìn)階學(xué)習(xí) 選擇符3. CSS Hack大全-教你如何區(qū)分出IE6-IE10、FireFox、Chrome、Opera4. 使用css實(shí)現(xiàn)全兼容tooltip提示框5. 低版本IE正常運(yùn)行HTML5+CSS3網(wǎng)站的3種解決方案6. 使用純HTML的通用數(shù)據(jù)管理和服務(wù)7. css代碼優(yōu)化的12個(gè)技巧8. 告別AJAX實(shí)現(xiàn)無(wú)刷新提交表單9. HTML DOM setInterval和clearInterval方法案例詳解10. CSS3實(shí)例分享之多重背景的實(shí)現(xiàn)(Multiple backgrounds)

 網(wǎng)公網(wǎng)安備
網(wǎng)公網(wǎng)安備